Chapter 12: Securing Your Serverless Application
- Integrate a user in a user pool with an identity pool to allow users to log in with their Facebook account.
Answer: In order to integrate Facebook with Amazon Cognito identity pools, you must follow the given procedure:
- Create a Facebook Application from the Facebook Developers portal (https://developers.facebook.com/).
- Copy the App ID and secret.
- Configure Facebook as a provider in Amazon Cognito Console:
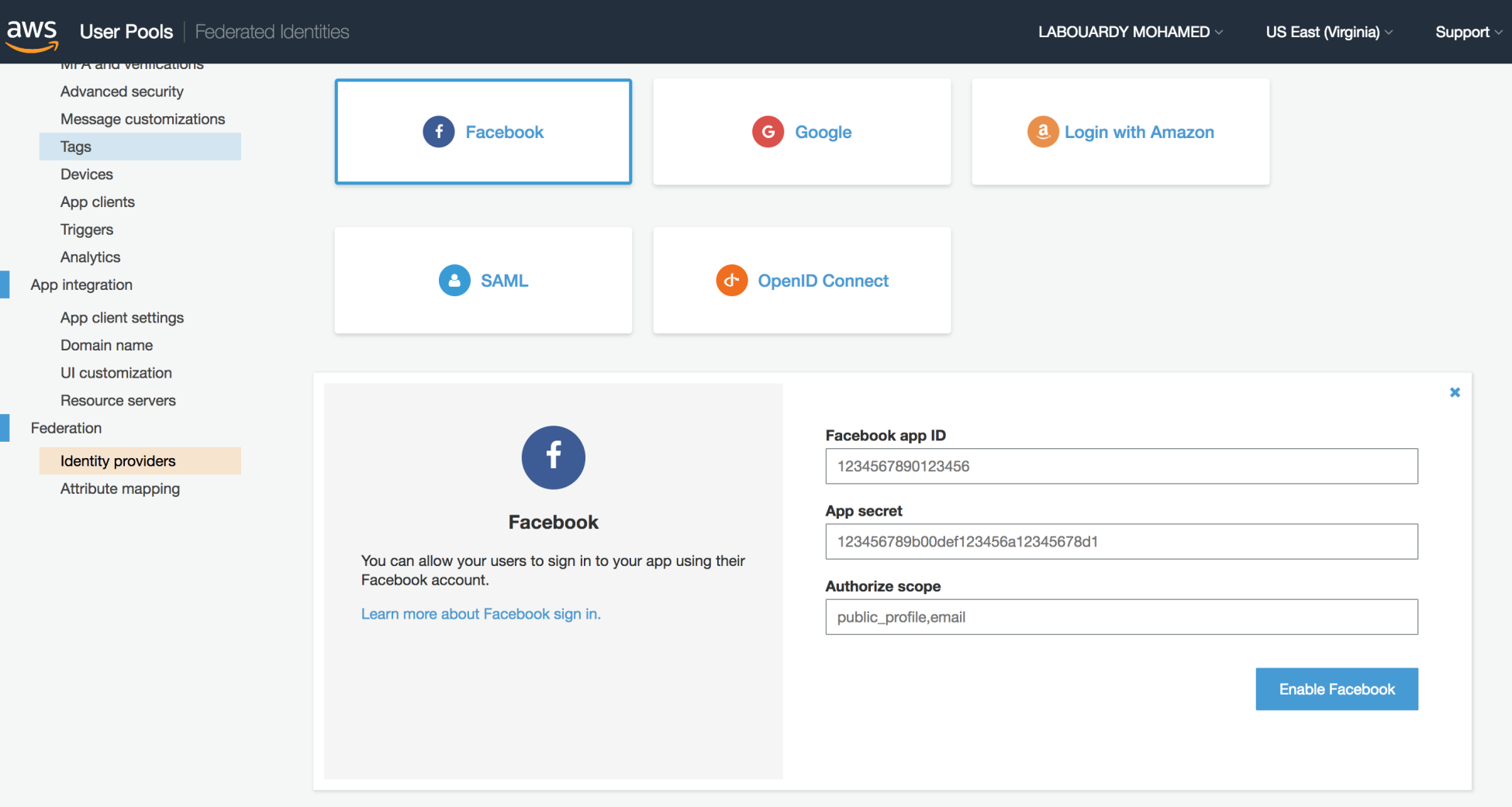
- Follow the Facebook Guide (https://developers.facebook.com/docs/facebook-login/login-flow-for-web/v2.3) to add the Facebook login button to the web application.
- Once the user is authenticated, a Facebook session token will be returned; this token must be added to the Amazon Cognito credentials provider to fetch a JWT token.
- Finally, add the JWT token to the API Gateway request
Authorizationheader.
- Integrate a user in a user pool with an identity pool to allow users to log in with their Twitter account.
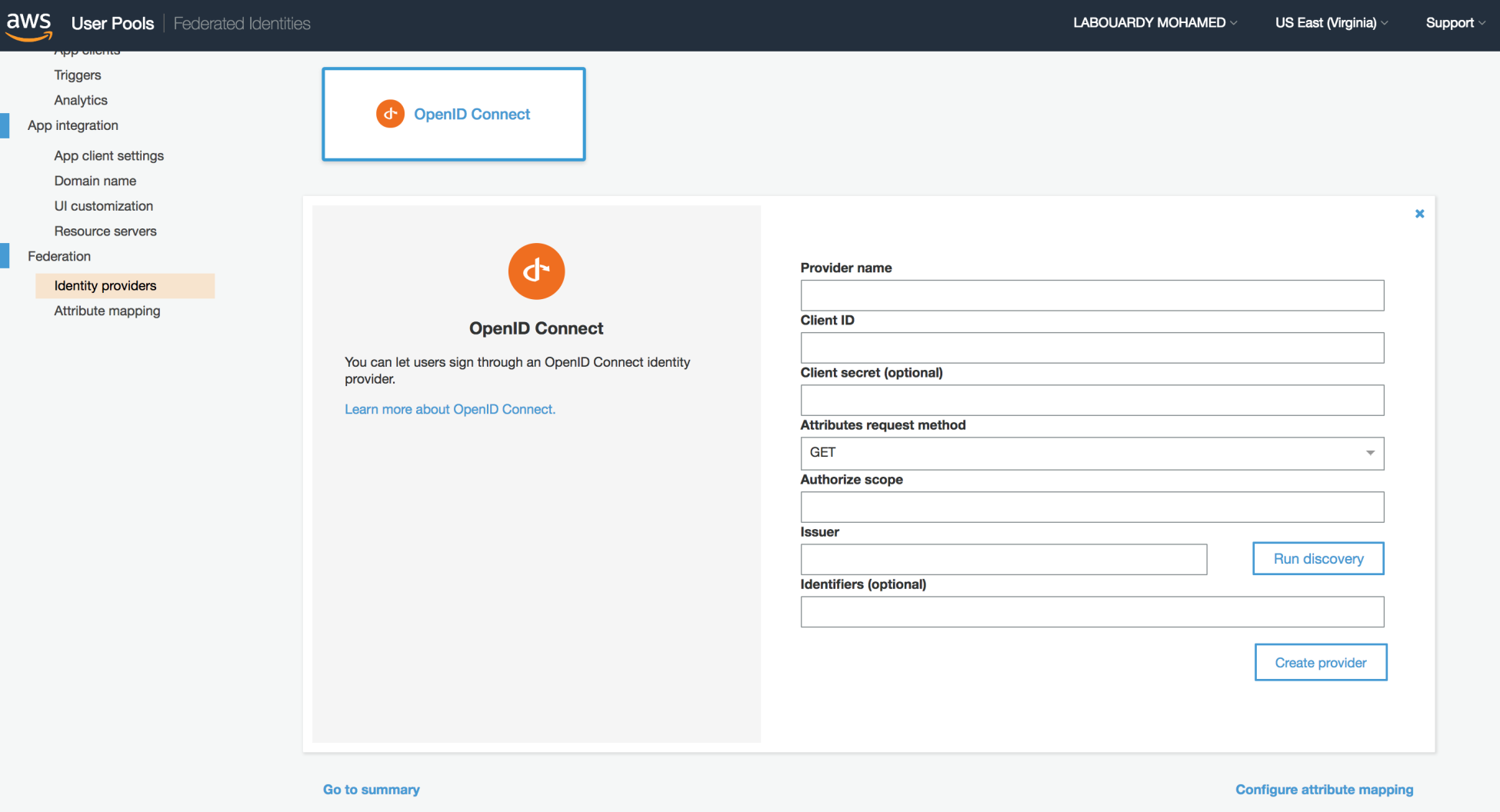
Answer: Amazon Cognito doesnot support Twitter as an authentication provider out of the box. Hence, you will need to use OpenID Connect to extend Amazon Cognito:
- Integrate a user in a user pool with an identity pool to allow users to log in with their Google account.
- To enable Google Sign in, you will need to create a new project from Google Developers Console (https://console.developers.google.com/)
- Enable the Google API under APIs and auth, and then create an OAuth 2.0 client ID.
- Configure Google in the Amazon Cognito Console:
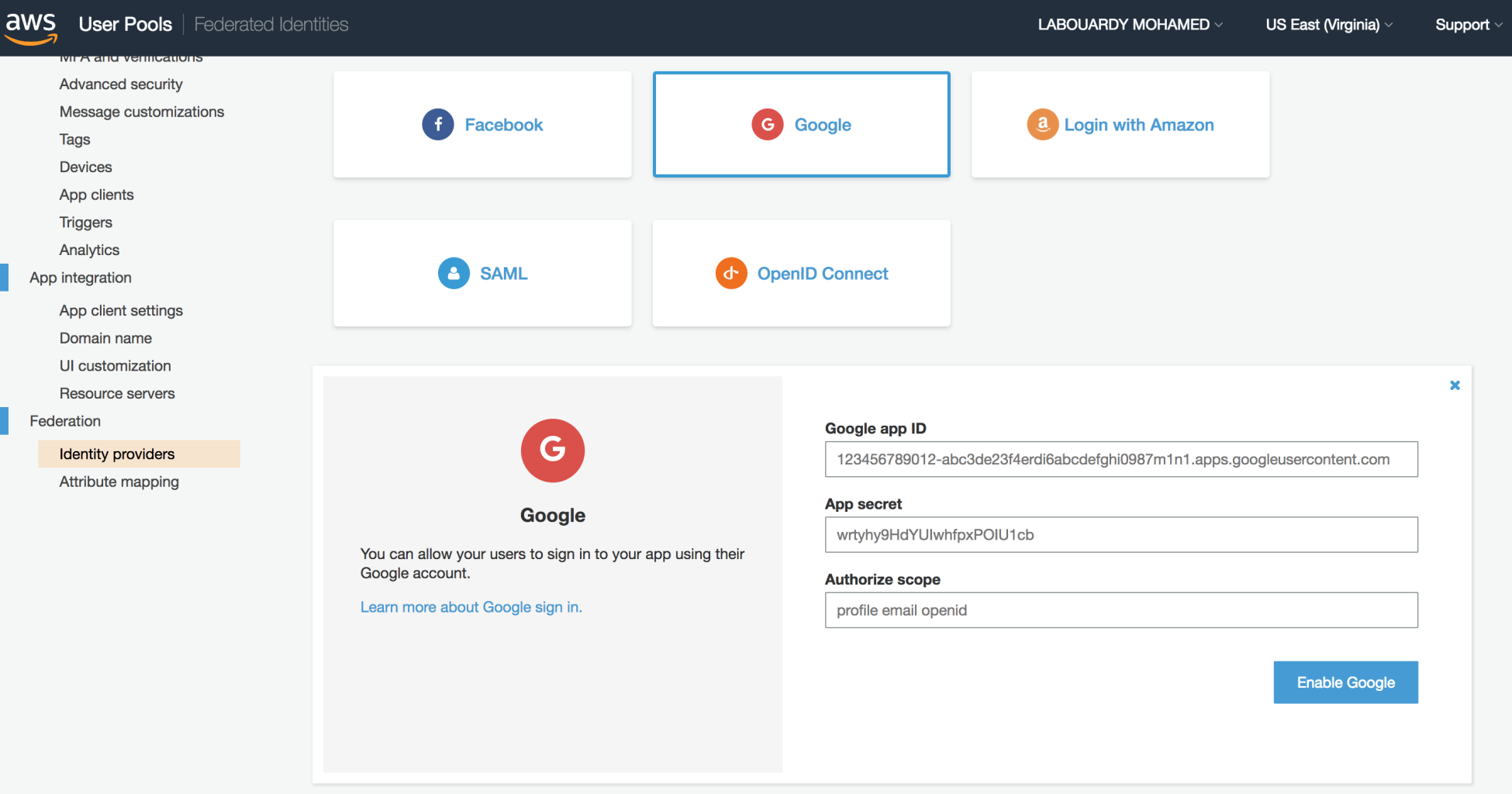
- Follow the Google documentation for Web (https://developers.google.com/identity/sign-in/web/sign-in) to add the Google sign in button.
- Once the user is authenticated, an authentication token will be generated, which can be used to retrieve the JWT token.
- Implement a form to allow users to create an account on a web application so that they are able to log in.
Answer: A Go based Lambda function might be created to handle the account creation workflow. The function's entry point is given as follows:
package main
import (
"os"
"github.com/aws/aws-lambda-go/lambda"
"github.com/aws/aws-sdk-go-v2/aws"
"github.com/aws/aws-sdk-go-v2/aws/external"
"github.com/aws/aws-sdk-go-v2/service/cognitoidentityprovider"
)
type Account struct {
Username string `json:"username"`
Password string `json:"password"`
}
func signUp(account Account) error {
cfg, err := external.LoadDefaultAWSConfig()
if err != nil {
return err
}
cognito := cognitoidentityprovider.New(cfg)
req := cognito.SignUpRequest(&cognitoidentityprovider.SignUpInput{
ClientId: aws.String(os.Getenv("COGNITO_CLIENT_ID")),
Username: aws.String(account.Username),
Password: aws.String(account.Password),
})
_, err = req.Send()
if err != nil {
return err
}
return nil
}
func main() {
lambda.Start(signUp)
}
- Implement a forgotten password flow for an unauthenticated user.
Answer: A Go based Lambda function might be created to reset user password. The function's entry point is given as follows:
package main
import (
"os"
"github.com/aws/aws-lambda-go/lambda"
"github.com/aws/aws-sdk-go-v2/aws"
"github.com/aws/aws-sdk-go-v2/aws/external"
"github.com/aws/aws-sdk-go-v2/service/cognitoidentityprovider"
)
type Account struct {
Username string `json:"username"`
}
func forgotPassword(account Account) error {
cfg, err := external.LoadDefaultAWSConfig()
if err != nil {
return err
}
cognito := cognitoidentityprovider.New(cfg)
req := cognito.ForgotPasswordRequest(&cognitoidentityprovider.ForgotPasswordInput{
ClientId: aws.String(os.Getenv("COGNITO_CLIENT_ID")),
Username: aws.String(account.Username),
})
_, err = req.Send()
if err != nil {
return err
}
return nil
}
func main() {
lambda.Start(forgotPassword)
}




































































