Accessing management
Once we have designed the network architecture, it's now time to understand how the servers will be placed in terms of DMZ and private environments.
Accordingly, the accessing methods will differ as well; with the general rule of thumb, all servers must be accessible via bastion host or VPN. Some organizations decide to open up port 22 for whitelisted office IPs for servers under DMZ but this is not the right approach.
Bastion hosts
Bastion hosts, also known as jump box, basically act as a proxy that allows the client to connect to remote servers. These remote servers are generally on a private subnet that is not accessible directly, with bastion generally being on the public subnet.
The following diagram shows the basic role of bastion hosts:
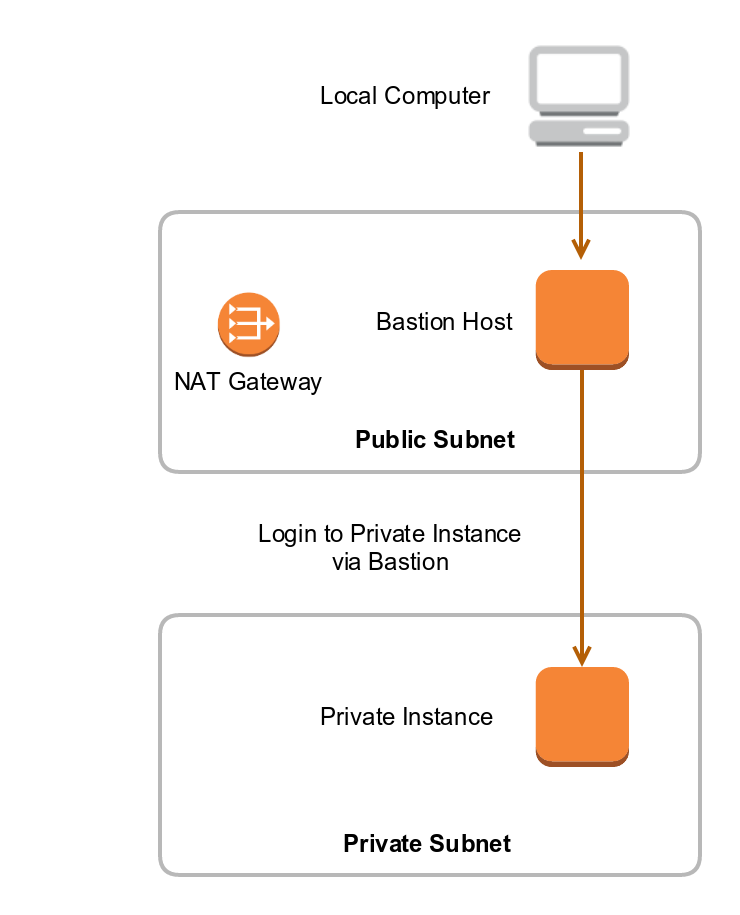
The client wants to connect to an instance in Private Subnet. As he cannot connect directly, he uses Bastion Host in the same network as a proxy to establish the connection to an instance in Private Subnet.





































































