Message authentication codes
When a message is sent from a sender to a receiver, how does the receiver know if the message is not tampered with in the process?
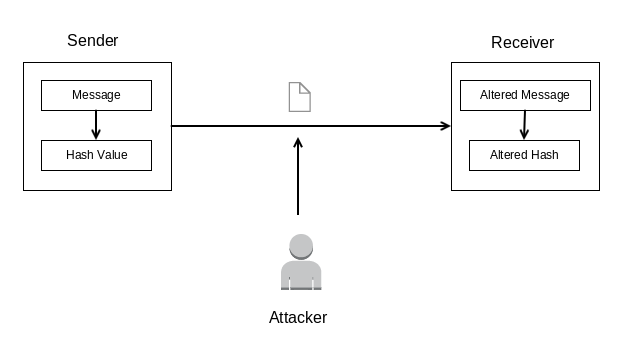
One simple answer is to include the Hash Value with the Message. However, an Attacker can modify the Hash Value along with the Message itself. This is demonstrated in the following diagram:
The MAC approach
In the MAC approach, the sender computes a MAC from the original message. A MAC can only be computed with the associated secret key.
One important property of MAC is that it is not possible to compute a MAC of a message without knowing the secret key associated:
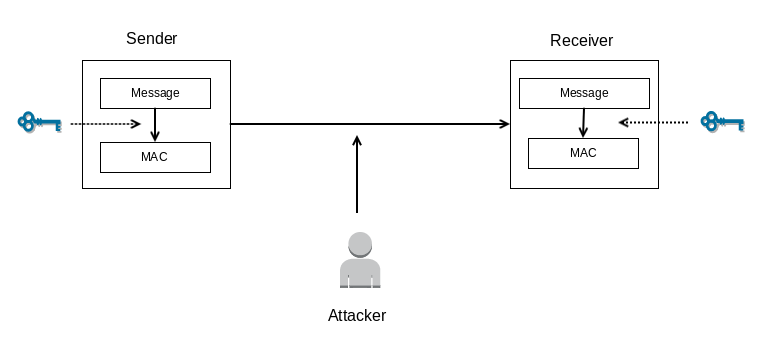
The Receiver has a key associated to decrypt the message. If the Attacker modifies the Message and MAC during the process, the receiver will not be able to compute the MAC from the key that he has. This means that the message is altered.
Note
For MAC, the secret key has to be known to both the sender and receiver.
The challenges with symmetric key storage
Ciphers, such as AES, are...





































































