Replacing the NSX Manager certificate
When you first deploy the NSX Manager, it creates a self-signed certificate. Using a self-signed certificate is generally not a recommended security practice. It is recommended to deploy a signed certificate from your internal certificate authority. NSX Manager supports two ways of deploying a signed certificate, which are as follows:
- Certificate signing request to a Certificate Authority (CA)
- Importing a PKCS#12 certificate archive (bundle) onto the NSX Manager, which includes the private and public key for NSX Manager and certificate chain of any subordinate CAs in your environment
In the following recipes, we will explore how you can create a certificate signing request on NSX Manager and how to import a PKCS#12 certificate bundle onto the NSX Manager.
Certificate Signing Request
A Certificate Signing Request (CSR) is the first part in a three-step process; this process involves the following steps:
- The NSX Manager creating a CSR
- The CSR is sent as a request to the certificate authority, which then signs the certificate and sends back a signed certificate
- Importing the signed certificate into the NSX Manager
How to do it...
The procedure to complete a certificate signing request is as follows:
- Log into NSX Manager via your web browser
- Click on
Manage Appliance Settings - Click on
SSL Certificates
- Click on
Generate CSRand follow the prompts as per the following screenshot:
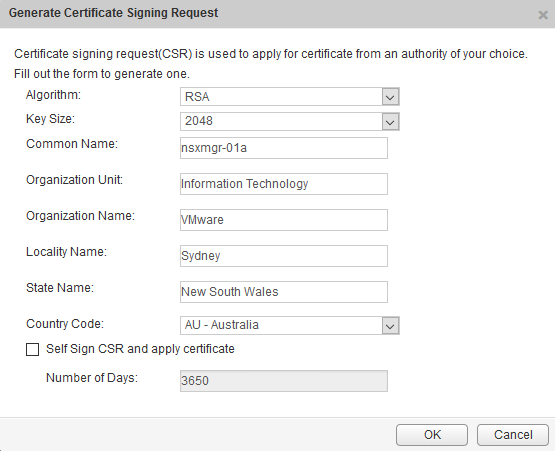
- Click on
OKand selectDownload CSR - Send the CSR file to your security administrator and get the certificate signed
- With the returned certificate, click on
Importso you can import the correct certificate into the NSX Manager - Reboot the NSX Manager to complete the process of importing a signed certificate into the NSX Manager
PKCS#12 certificate
Importing PKCS#12 into the NSX Manager is used when the certificate signing was not completed using the CSR method outlined in the previous recipe. The PKCS#12 format is typically used in scripted installations of NSX Manager and other components. If a CSR was not generated by the NSX Manager itself, it is required that the PKCS#12 archive is imported into NSX Manager.
The PKCS#12 archive generally consists of the following:
- A signed server certificate
- A private key for the signed certificate
- Root and intermediate certificate authority public keys
The PKCS#12 is also password-protected, so it's important to have the password before attempting to import the PKCS#12 archive into NSX Manager.
In some cases, the received signed certificate may not be in the PCKS#12 format. In this event, you must convert the certificates into the PKCS#12 format for import into the NSX Manager. This can be achieved using openSSL (https://www.openssl.org/), and the command to achieve this is as follows:
openssl pkcs12 -export -out server.p12 -inkey server.key -in server.crt -certfile CACert.crtHow to do it...
The procedure to import the PCKS#12 archive is as follows:
- Log into the NSX Manager via your web browser
- Click on
Manage Appliance Settings - Click on
SSL Certificates - Click on
Upload PCKS#12Keystoreand browse to the file - Enter the password for archive and click on
Import - Reboot the NSX Manager to complete the process of importing the signed certificate





































































