The OWASP Top 10
Among the previously mentioned proposals, the so-called OWASP Top 10 is by far the most requested among programmers all over the world.
Its main goal is to help developers identify the most critical security risks facing organizations. To help in the task, they publish a periodical bulletin which has been published since they started in 2010. The current, updated version is the 2013 edition, although they're working on a version for 2017, which is not available at the time of writing this.
The top 10 vulnerabilities are presented in the following graphic. It assumes that the ordering is important, the first one being the most used or dangerous (or both, in many cases):
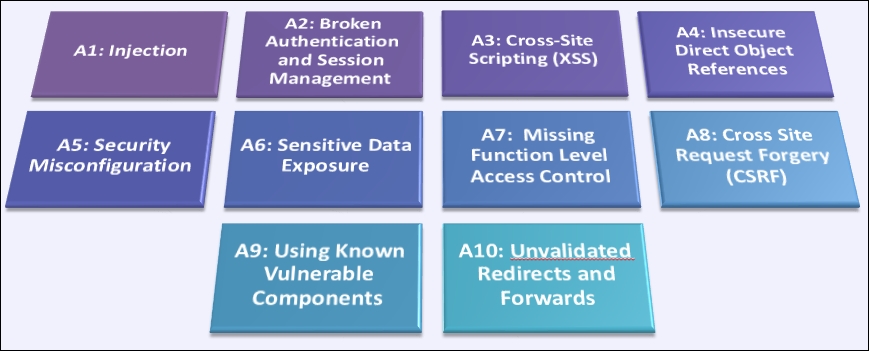
Also, keep in mind that often, an attack can be a compound of different steps, each step using some of these vulnerabilities (this happens in some of the most sophisticated attacks we know of).
In the diagram, OWASP explains a use case in which an actor gets access to a valuable resource and the elements involved...
























































