Firewall identification with Nmap
Nmap has a streamlined firewall filtering identification function that can be used to identify filtering on ports based on ACK probe responses. This function can be used to test a single port or multiple ports in sequence to determine filtering status.
Getting ready
To use Nmap to perform firewall identification, you will need to have a remote system that is running network services. Additionally, you will need to implement some type of filtering mechanism. This can be done with an independent firewall device or with host-based filtering such as Windows Firewall. By manipulating the filtering settings on the firewall device, you should be able to modify the results of the scans.
How to do it…
These steps will help you to identify firewall using the Nmap:
- To perform an Nmap firewall ACK scan,
nmapshould be called with the IP address specification, the destination port, and the-sAoption:
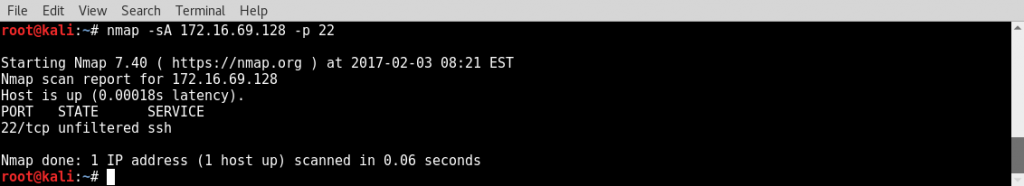
- On performing this scan on the Metasploitable2 system in my local network...




































































