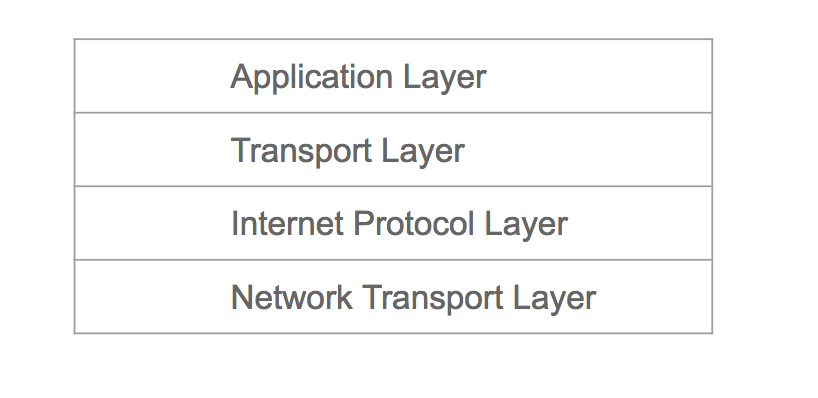
The TCP/IP model
It is necessary to understand the communication models because fundamentally, the network traffic is assembled, packaged, and de-assembled based on these models.
Each protocol operates at a specific layer. Depending upon the protocols being used, the security controls are needed accordingly. This is the reason why one should have a good understanding of the layers of the TCP/IP model.
Before we start working on security controls, let's understand the basic architecture of the TCP/IP model:
In order to understand how exactly layering works, we will look at an example of a Wireshark packet capture.
Scenario
We started our Wireshark packet capture and visited kplabs.in via browser. Then, we captured a sample packet and deconstructed it to understand how it works. There are four primary layers that you see in the packet capture:
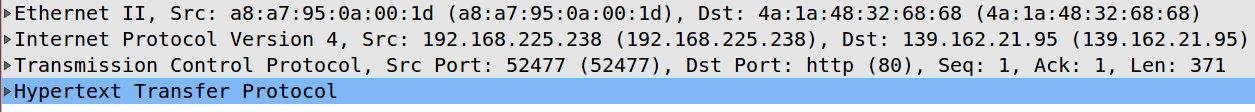
The Network Transport Layer
The Network Transport Layer is the first layer of the TCP/IP model and the same is reflected in the packet data. This layer defines...





































































