Encrypting and storing passwords correctly
One thing I have often seen is badly stored passwords. Just because the password is stored in a database on your server, does not make it secure. So what do badly stored passwords look like?
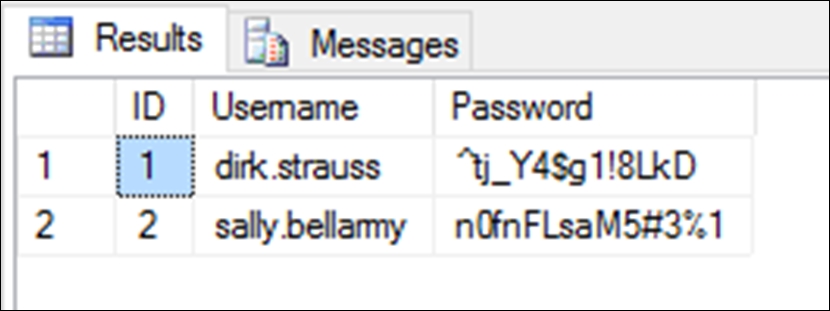
Secure passwords stored badly are no longer secure. The passwords in the previous screenshot are the actual user passwords. Entering the first password, ^tj_Y4$g1!8LkD at the login screen will give the user access to the system. Passwords should be stored securely in the database. In fact, you need to employ salted password hashing. You should be able to encrypt the user's password, but never decrypt it.
So how do you decrypt the password to match it to the password the user enters at the login screen? Well, you don't. You always hash the password the user enters at the login screen. If it matches the hash of their real password stored in the database, you give them access to the system.
Getting ready
The SQL tables in this recipe are for illustration only and are...
























































