Windows memory layout
The Windows OS memory has a number of sections that can be considered as the high-level components. To write exploits and take advantage of vulnerable programs, we have to understand the memory structure and its sections.
Getting ready
Before starting the exploit script writing, we have to get an idea about the structure of the Windows memory layout.
Let's have a look at the memory structure for an executable:
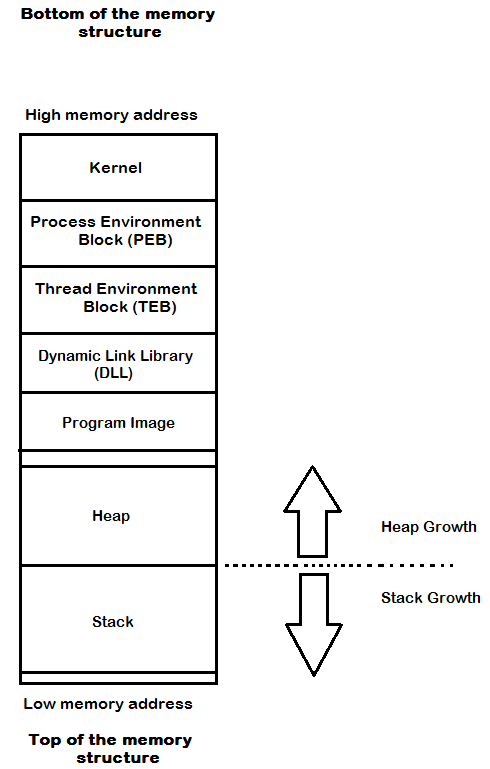
As we use a stack and heap in most cases of exploits, we can start with these.
The stack
The stack is used for short-term local storage in an ordered manner. Each thread in an application has a stack. A unique stack with a fixed size is assigned for a thread or a function when it is called. The size of the stack is defined when the application or thread starts. Also, this stack gets destroyed when this function or thread gets finished. The stack is mainly used to store local variables, save function return pointers, function argument exception handler records, and much...




































































