Insecure Protocols and Their Use Cases
In this section, we are going to look in detail at the different insecure protocols and their use cases.
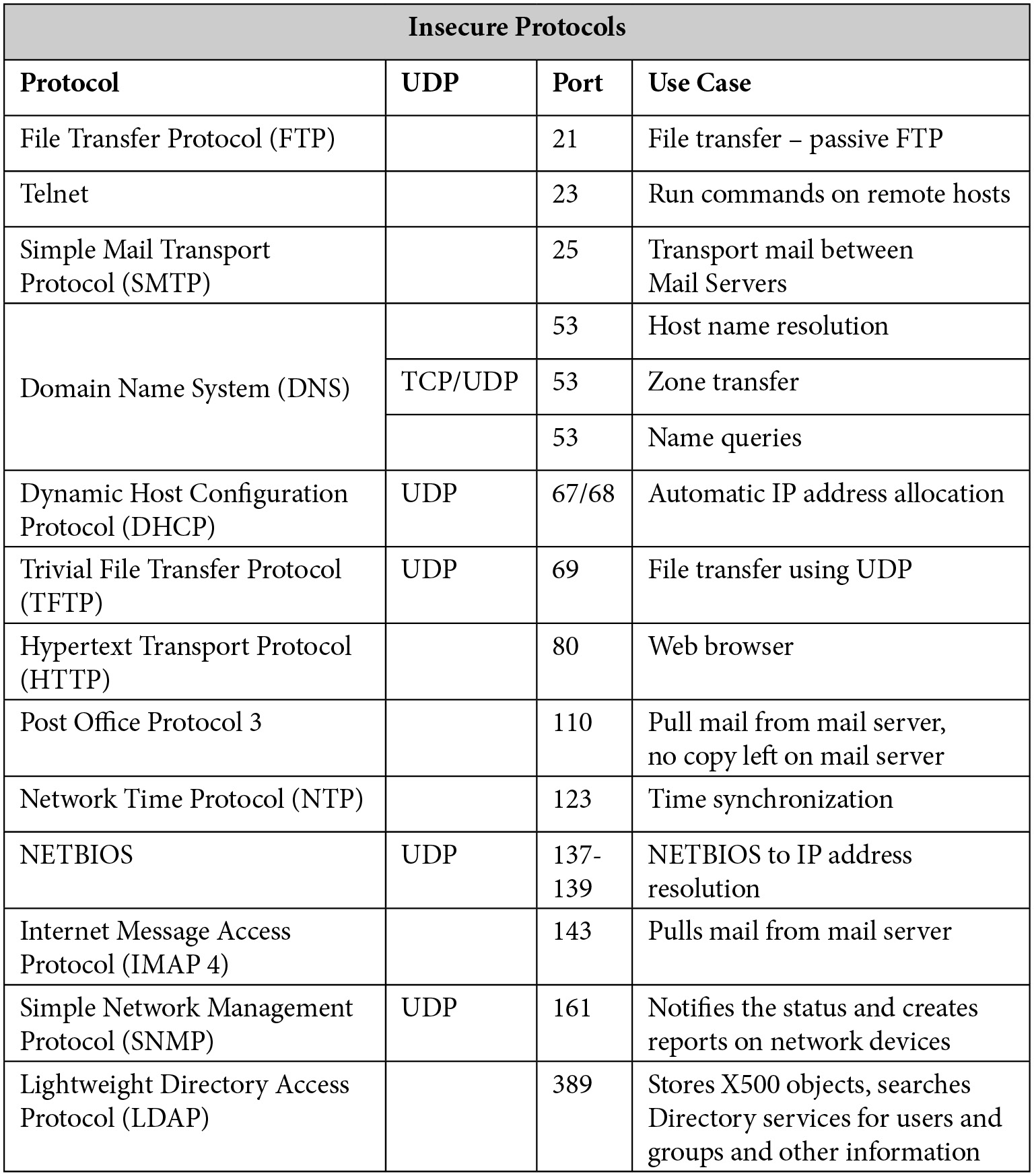
Let's look at each of them:
- FTP: Transferring files is a common function. When we purchase an e-book, it is immediately available to download onto our Kindle. If I wish to upload files to a web server, I would use FTP on port
20, but the more common use is to download files using port21, which is known as Passive FTP. The downside of using FTP is that the transfer is done using clear text, so a packet sniffer could view the information. It could be replaced by secure protocols such as SFTP or FTPS. - Telnet: This is a protocol that was first used in 1973 to run remote commands on devices such as routers. Unfortunately, the session is in clear text and therefore not secure. If you want to know whether port
25is open on a mail server called Mail1, you could runtelnet Mail1 25. It is no longer used...





































































