Understanding Digital Forensics
Digital forensics is used by the police when they are investigating crimes and need to find digital evidence so that they can secure a conviction. We will be looking at computer- and web-based attacks.
In 2006, Forensic Process 19, proposed by NIST, consisted of four different phases: collection, examination, analysis, and reporting. Here's a diagram showing these phases:
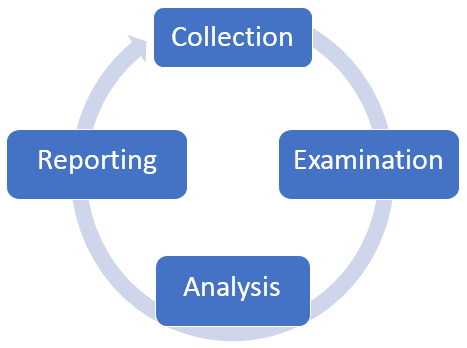
Figure 1.6 – Forensics cycle
Let's look at each of these phases:
- Collection: Here, the data is examined, then extracted from the media that it is on, and then converted into a format that can be examined by forensic tools.
- Examination: Prior to examination, the data will be hashed, and then an investigation will be carried out with the relevant forensic tool. When the examination has concluded, the data is once again hashed to ensure that the examiner or the tools have not tampered with it. We could use a USB write blocker that allows only read access to storage media.
- Analysis: When all of the forensic data has been collected, it is analyzed and then transformed into information that can be used as evidence.
- Reporting: A report is compiled that can be used as evidence for conviction.
There are many different components to a forensic investigation; we will look at each of them in turn:
- Admissibility: All evidence relevant to the case is deemed admissible only if it is relevant to the disputed facts of the case and does not violate any laws or legal statutes.
- Order of Volatility: Say you are a firefighter and you arrive at a house on fire; you can only save items one at a time and there are two items inside. The first is a snowman, and the second is a rib of beef. You now have a dilemma: which one should you choose? Easy! You save the snowman first as it is melting, and you let the rib of beef cook some more so that the other firefighters can have a nice supper! So, when we want to ascertain the order of volatility, we are looking to secure the most perishable evidence first. We do not try and stop the attack until we have secured the volatile evidence so that the source can be identified. This is known as the order of volatility. Let's look at a few examples.
Example 1 – Web-Based Attack: An attacker is attacking the company website and the security team is trying to capture the network traffic to find the source of the attack. This is the most volatile evidence.
Example 2 – Attack inside a Computer: When someone has attacked your computer, you need to capture the evidence in accordance with the order of volatility:
a. CPU Cache: Fast block of volatile memory used by the CPU
b. Random Access Memory (RAM): Volatile memory used to run applications
c. Swap/Page File/Virtual Memory: Used for running applications when RAM is totally exhausted.
d. Hard Drive: Data at rest for storing data
Example 3 – Removable Storage Drive Attached to a Computer/Server: Someone has left a USB flash drive plugged into your fileserver. When it is in use, programs such as Word are launched in RAM, so we would capture the volatile memory first.
Example 4 – Command-Line Tools: You need to know which command-line tool provides information that could disappear if you reboot the computer, and that would be
netstat. Withnetstat -an, the listening and established ports are shown. If you reboot the computer, all of the established connections will be lost.Tip
Order of volatility is collecting the most perishable evidence first. In a web-based attack, we should collect the network traffic with a packet sniffer.
Five-Minute Practical
Open up Command Prompt on your computer and type netstat -an. You should now see the listening and established ports; count them, and write the numbers down. Run the shutdown /r /t 0 command to immediately reboot the machine. Log back in, go to Command Prompt, and run netstat -an; what is the difference? You will see that you have lost information that could have been used as evidence.
Collection of Evidence
In this section, we will look at different types of evidence collection:
- E-Discovery: During e-discovery, companies may be subpoenaed so that we can collect, review, and interpret electronic documents located on hard disks, USB drives, and other forms of storage.
- Chain of Custody: The chain of custody is one of the most crucial aspects of digital forensics, ensuring the evidence has been collected and there is not a break in the chain. It starts when the evidence has been collected, bagged, tied, and tagged, ensuring the evidence has not been tampered with. It lists the evidence and who has handled it along the way. For example, Sergeant Smith handed 15 kg of illegal substance to Sergeant Jones following a drugs raid. However, when it is handed in to the property room, 1 kg is missing. In this event, we would need to investigate the chain of custody. In this scenario, Sergeant Jones would be liable for the loss. Chain of custody examples are as follows:
Example 1 – Missing Entry on the Chain of Custody Document: On Monday, 15 laptops were collected by the system administrator. The next day, the system administrator passed them on to the IT manager. On Wednesday, the IT director presents the 15 laptops as evidence to the court. The judge looks at the chain of custody document and notices that there was no formal handover between the IT manager and the IT director. With the handover missing, the judge wants to investigate the chain of custody.
Example 2 – Evidence Leaves the Detective's Possession: The FBI arrests a known criminal and collects 43 hard drives that they bag and tag, before placing them in two bags. They arrest the criminal and take him from Arizona to New York by airplane. One detective is handcuffed to the criminal while the other carries the two bags.
When they arrived at check-in, the airline clerk tells them that the carry-on bags are more than the 8 kg allowance, and therefore they are too heavy and need to go in the hold. The detective complies, but locks the suitcases to prevent theft. Because the evidence is not physically in their possession at all times, the chain of custody is broken as there is a chance that someone working for the airline could tamper with the evidence. Therefore, they cannot prove to the court that the integrity of the evidence has been kept intact at all times.
- Provenance: When the chain of custody has been carried out properly and the original data presented to the court has not been tampered with, it is known as data provenance.
- Legal Hold: Legal hold is the process of protecting any documents that can be used in evidence from being altered or destroyed. Sometimes, this is also known as litigation hold.
Example: Dr. Death has been prescribing new drugs to patients in a large hospital who have been dying. An auditor has been sent to investigate the possibility of foul play, and then following the audit, the FBI is notified. The doctor has been emailing a pharmaceutical company that has been supplying the drugs for a trial. The FBI does not want the doctor to be alerted, so they have the hospital's IT team put his mailbox on legal hold. When the mailbox is on legal hold, the mailbox limit is lifted; the doctor can still send and receive emails, but cannot delete anything. This way, they are not alerted to the fact that they are under investigation.
- Data Acquisition: This is the process of collecting all of the evidence from devices, such as USB flash drives, cameras, and computers; as well as data in paper format, such as letters and bank statements. The first step in data acquisition is to collect the volatile evidence so that it is secured. The data must be bagged and tagged and included in the evidence log.
- Artifacts: This can be log files, registry hives, DNA, fingerprints, or fibers of clothing normally invisible to the naked eye.
- Time Offset: When we collect evidence from computers, we should record the time offset. This is the regional time so that in a multinational investigation, we can put them into a time sequence—this is known as time normalization.
- Time Normalization: This is where evidence is collected across multiple time zones, then a common time zone, such as GMT, is used so that it can be put into a meaningful sequence.
Example: The police in three separate countries are trying to identify where the data started from in a chain, then who handled the data along the line. They have the following information about when it was first created:
a. New York: Created 3 a.m.
b. London: Created 4 a.m.
c. Berlin: Created 4.30 a.m.
By recording the time offset, it looks as if it started off in New York, but if we apply time normalization, when it is 4 a.m. in London, the time in New York is 11 p.m. the day before, so it cannot be New York. When it is 4.30 a.m. in Berlin, it is only 3.30 a.m. in London; therefore, it originated in Berlin. This looked the least unlikely before the time offset of the data collection had time normalization applied.
- Time Stamps: Each file has time stamps showing when files were created, last modified, and last accessed:
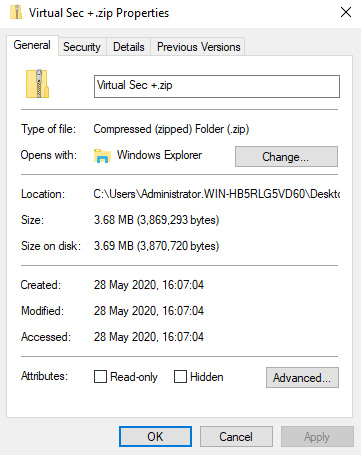
Figure 1.7 – Time stamps
- Forensic Copies: If we are going to analyze removable data that we have acquired, we would first of all take a forensic copy and keep the original data intact. We would then use the copy to analyze the data so that we keep the original data unaltered, as it needs to be used in its original state and presented as evidence to the courts. It would be hashed at the beginning and the end to confirm that the evidence has not been tampered with.
- Capturing System Images: When the police are taking evidence from laptops and desktops, they take a complete system image. The original image is kept intact and the system is analyzed to find evidence of any criminal activity. It would be hashed at the beginning and the end to confirm that the evidence has not been tampered with.
- Firmware: Firmware, sometimes called embedded systems, could be reversed engineered by an attacker, therefore it is important that we compare the source code that the developer wrote against the current source code in use. We would employ a coding expert to compare both lots of source code in a technique called regression testing. Types of attacks that affect embedded systems could be rootkit and backdoor.
- Snapshots: If the evidence is from a virtual machine, a snapshot of the virtual machine can be exported for investigation.
- Screenshots: You may also take screenshots of applications or viruses on the desktops and keep them as evidence. A better way of doing this would be to use a modern smartphone that would geotag the evidence.
Tip
You should capture a system image from a laptop and take a forensic copy from a removable drive
- Taking Hashes: When either the forensic copy or the system image is being analyzed, the data and applications are hashed at the beginning of the investigation. It can be used as a checksum to ensure integrity. At the end, it is re-hashed and should match the original hash value to prove data integrity.
- Network Traffic and Logs: When investigating a web-based or remote attack, we should first capture the volatile network traffic before stopping the attack. This will help us identify the source of the attack. In addition to this, we should look at different log files from the firewall, NIPS, NIDS, and any server involved. If we use a Security Information Event Management (SIEM) system, this can help collate these entries and give a good picture of any attack. However, if it is a rapidly expanding virus, we would quarantine it.
Example: Your company uses an account lockout of three attempts. If an attacker tries to log in once to three separate computers, each computer would not identify it as an attack, as it is a single attempt on each computer, but a SIEM system would pick up these attempts as three failed logins attempts and alert the administrators in real time.
Tip
You should remove a computer with a dynamically expanding virus immediately rather than collect the network traffic.
- Capturing Video: CCTV can be a good source of evidence for helping to identify attackers and the time the attack was launched. This can be vital in apprehending suspects.
- Interviews: The police may also take witness statements to try and get a picture of who was involved and maybe then use photo-fits so that they can be apprehended.
- Preservation: Data needs to be preserved in its original state so that it can be produced as evidence in court. This is why we take copies and analyze the copies so that the original data is not altered and is pristine. Putting a copy of the most vital evidence in a WORM drive will prevent any tampering with the evidence, as you cannot delete data from a WORM drive. You could also write-protect the storage drives.
- Recovery: When the incident has been eradicated, we may have to recover the data from a backup; a faster method would be a hot site that is already up and running with data less than 1 hour old. We may also have to purchase additional hardware if the original hardware was damaged during the incident.
- Strategic Intelligence/Counterintelligence Gathering: This is where different governments exchange data about cyber criminals so that they can work together to reduce threats. It is also possible for companies who have suffered an attack to log as much information as they can and have a third party who specializes in incident response to help them find a way to prevent re-occurrence.
- Active Logging: To track incidents, we need to be actively monitoring and actively logging changes to patterns in our log files or traffic patterns in our network. Installing a SIEM system that provides real-time monitoring can help collate all entries in the log files, ensuring that duplicate data is not used so that a true picture can be taken. Alerts based on certain triggers can be set up on our SIEM system so that we are notified as soon as the event happens.
Cloud Forensics
In the last few years, the growth of cloud computing and resources has been increasing year on year. Cloud forensics has different needs than that of traditional forensics. One of the primary aspects that a cloud provider must provide is security of the data stored in the cloud.
In 2012, Cloud Forensic Process 26 was created to focus on the competence and admissibility of evidence. The stages are as follows:
- Stage A – Verify the purpose of cloud forensics.
- Stage B – Verify the type of cloud service.
- Stage C – Verify the type of technology behind the cloud.
- Stage D – Verify the role of the user and negotiate with the Cloud Service Provider (CSP) to collect the evidence required.
Cloud services, because of the nature of their business, create virtual machines and then destroy them on a regular basis. This prevents the collection of forensic evidence. The forensic team needs to prove to the cloud provider their reasons for the collection of the evidence and they have to rely on the cloud provider sending them the correct evidence that they require.
Right-to-Audit Clauses
By inserting right-to-audit clauses into supply chain contracts, an auditor can visit the premises without notice and inspect the contractor's books and records to ensure that the contractor is complying with its obligation under the contract. This would help them identify the following:
- Faulty or inferior quality of goods
- Short shipments
- Goods not delivered
- Kickbacks
- Gifts and gratuities to company employees
- Commissions to brokers and others
- Services allegedly performed that weren't needed in the first place, such as equipment repairs
Regulatory and Jurisdiction
Cloud data should be stored and have data sovereignty in regions. The US introduced the CLOUD Act in 2018 due to the problems that the FBI faced in forcing Microsoft to hand over data stored in Ireland. In 2019, the UK received royal assent for the Overseas Production Act (COPOA), which allows the UK to seek data stored overseas as part of a criminal investigation. In 2019, the US and the UK signed a data-sharing agreement to give law enforcement agencies in each country faster access to evidence held by providers, such as social media or web hosting. In 2016, a similar agreement was set between the US and the EU; however, with the introduction of General Data Protection Regulation (GDPR), all websites in the US that have consumers from the EU have to abide by GDPR.
Data Breach Notifications/Laws
If a data breach occurs, a company can be fined more than £10 million for failing to report a breach. The EU uses GDPR, and notifications of data breaches must be reported within 72 hours. Other countries have their own reporting timescale.






































































