Working with Ghost Phisher
Similar to Fluxion, Kali has an inbuilt application to perform the Wi-Fi phishing activity in a GUI fashion. Ghost Phisher is built to identify wireless and Ethernet security auditing. It is written entirely in Python and Python QT for the GUI library.
In order to harvest user credentials, attackers can utilize the Ghost Phisher application to launch a Fake AP as shown in the following screenshot:
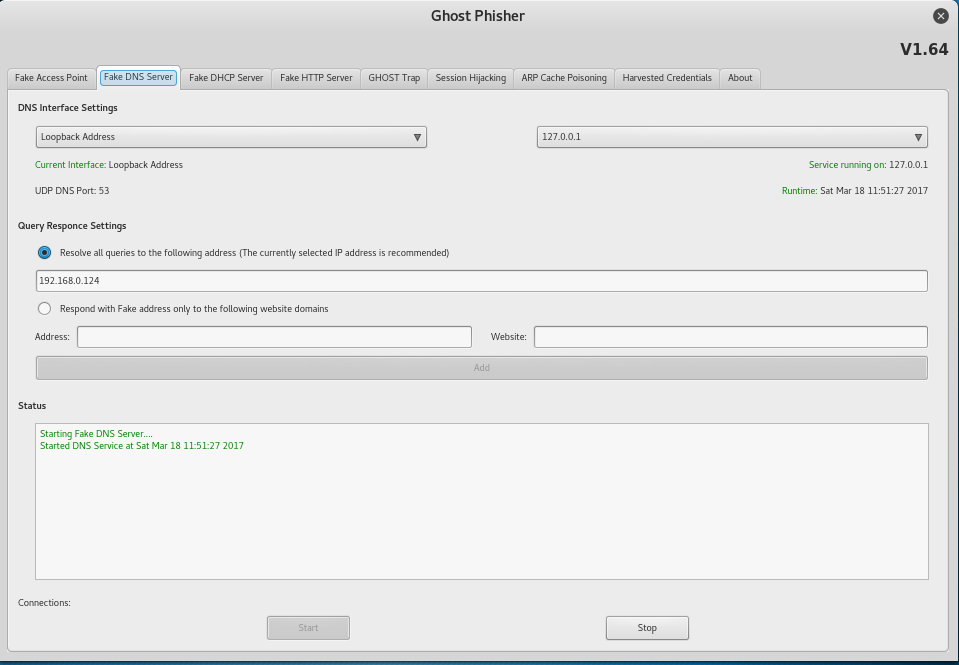
Ghost Phisher currently provides the following features that can be utilized by penetration testers or attackers:
- Creating an HTTP server
- DNS server
- DHCP server
- Credential logging page (for phishing any username and password)
- Access point emulator
- Advanced session hijacking module
- Ghost Phisher provides the option to perform ARP cache poisoning to perform MiTM and DoS attacks, similar to Ettercap/BetterCAP.
- Allows attackers to embed metasploit binding techniques
- A SQLite database as credentials storage.





































































