Information gathering with Sparta
Sparta offers a great deal of functionality out of the box. In this recipe, we will take a look at the Sparta interface, explore what Sparta does by default when you add hosts to the scope, look at some of the tools Sparta utilizes, and brute-force passwords.
Getting ready
Sparta comes pre-bundled with Kali Linux 2. To use it to perform scans, you will need to have a remote system that is running network services. In the examples provided, an instance of Metasploitable2 is used to perform this task. For more information on how to set up Metasploitable2, refer to Chapter 1, Getting Started.
How to do it...
Let's now dive straight into Sparta:
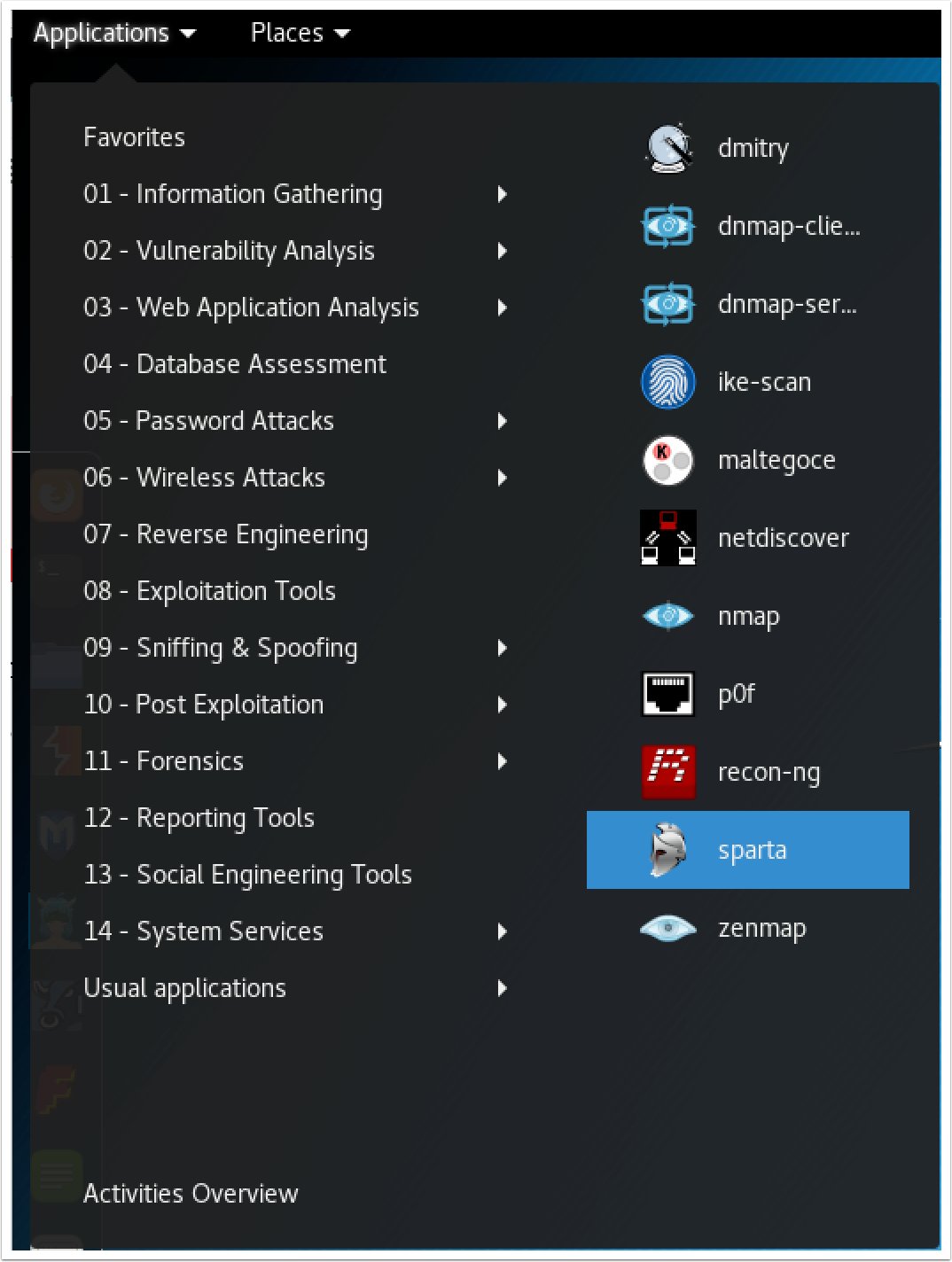
- To get started, navigate to
Applications|Information Gathering|sparta:
- Once Sparta has started, we need to define our target. In the
Hostspane, selectClick here to add host(s) to scope. For our examples, we will be using an IP address of172.16.69.128:
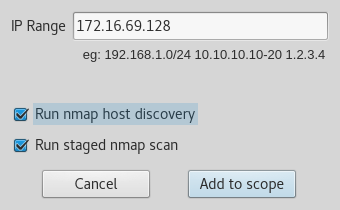
- Once you click on the
Add to scopebutton, the scans begin. First...




































































