Port scanning with hping3 (stealth)
In addition to the discovery techniques that we've learned, the hping3 command can also be used to perform port scans. This specific recipe demonstrates how we can use the hping3 command to perform a TCP stealth scan.
Getting ready
To use the hping3 command to perform a TCP stealth scan, you will need to have a remote system that is running accessible network services over TCP. In the examples provided, an instance of Metasploitable2 is used to perform this task. For more information on how to set up Metasploitable2, refer to Chapter 1, Getting Started.
How to do it…
In addition to the discovery capabilities that have already been mentioned, the hping3 command can also be used to perform a TCP port scan:
- To perform a port scan with
hping3, we need to use the--scanmode with an integer value to indicate the port number to be scanned:
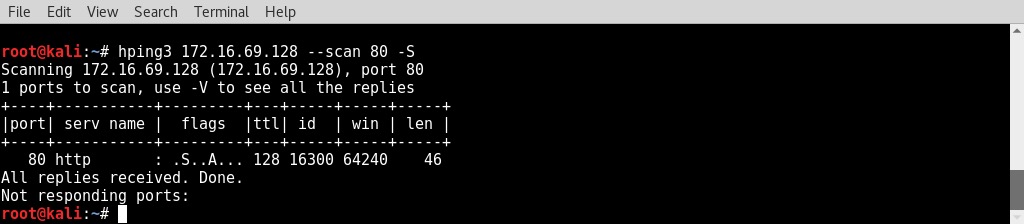
- In the example provided, a SYN scan was performed against the TCP port
80of the IP address indicated. The-Soption identifies...




































































