SET browser exploit lab
In this lab, we will demonstrate how to use SET to deliver a payload through a victim's web browser using Autopwn. For this lab, we are using Kali Linux running in VMware as our attacking machine. Our victim will be a Windows 7 machine running in VMware. We will provide screenshots for each step:
- First, we need to open SET by opening a Terminal and typing
setoolkit. On the first options menu screen type1forSocial-Engineering Attacks. The following screenshot displays the first options menu you will see:
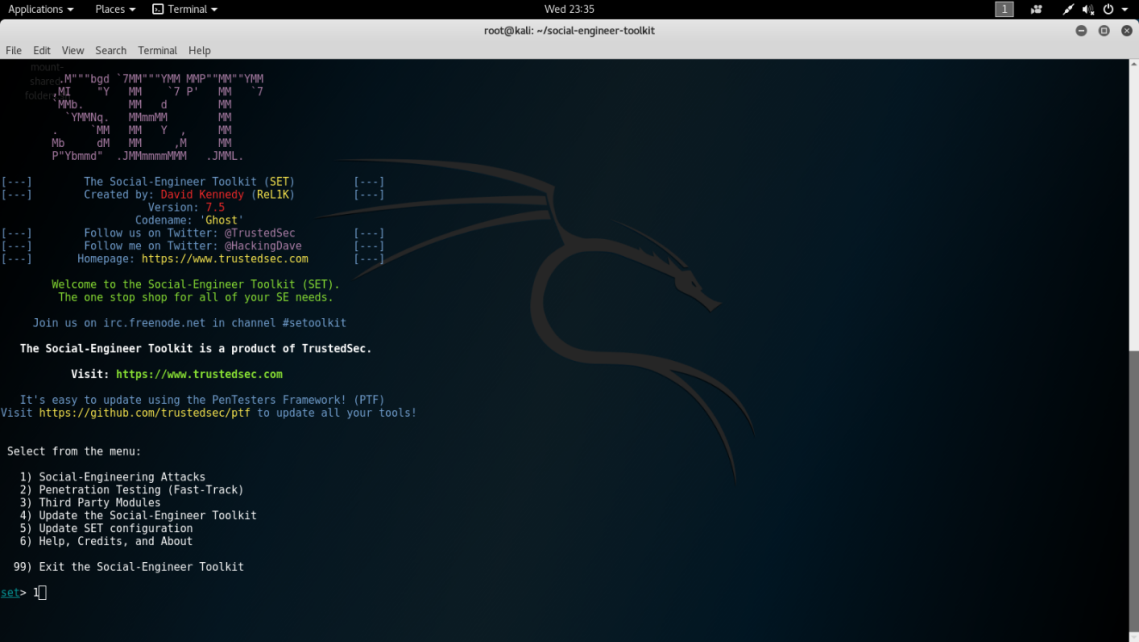
- On the next menu options screen, we will type
2forWebsite AttackVectors. The following screenshot displays the second options menu you will encounter:
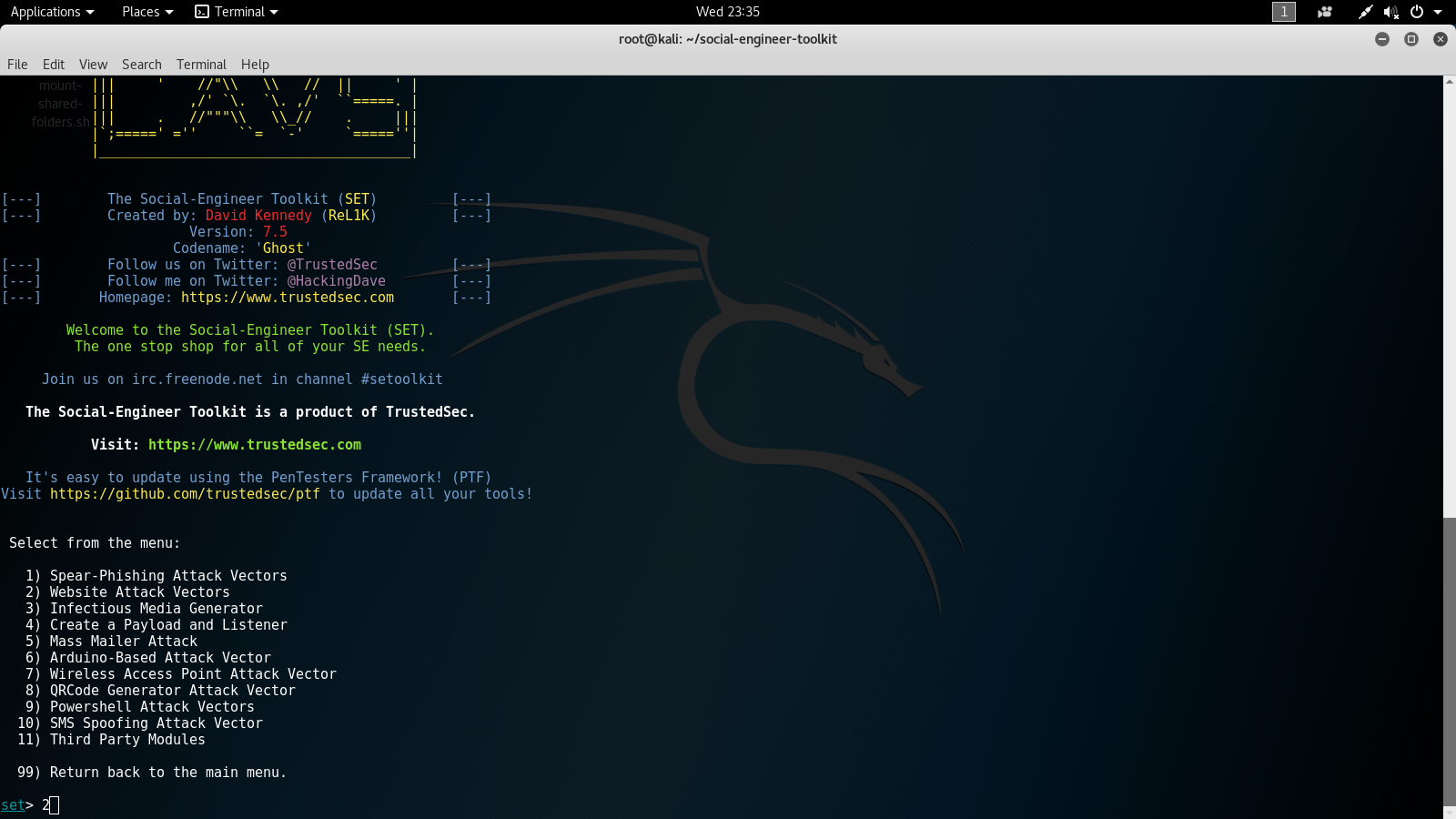
- The next options menu will ask us to choose an attack method. For this lab, we will choose number
2for theMetasploit Browser Exploit Method. The following screenshot displays what the third options menu will look like when selecting the attack method:
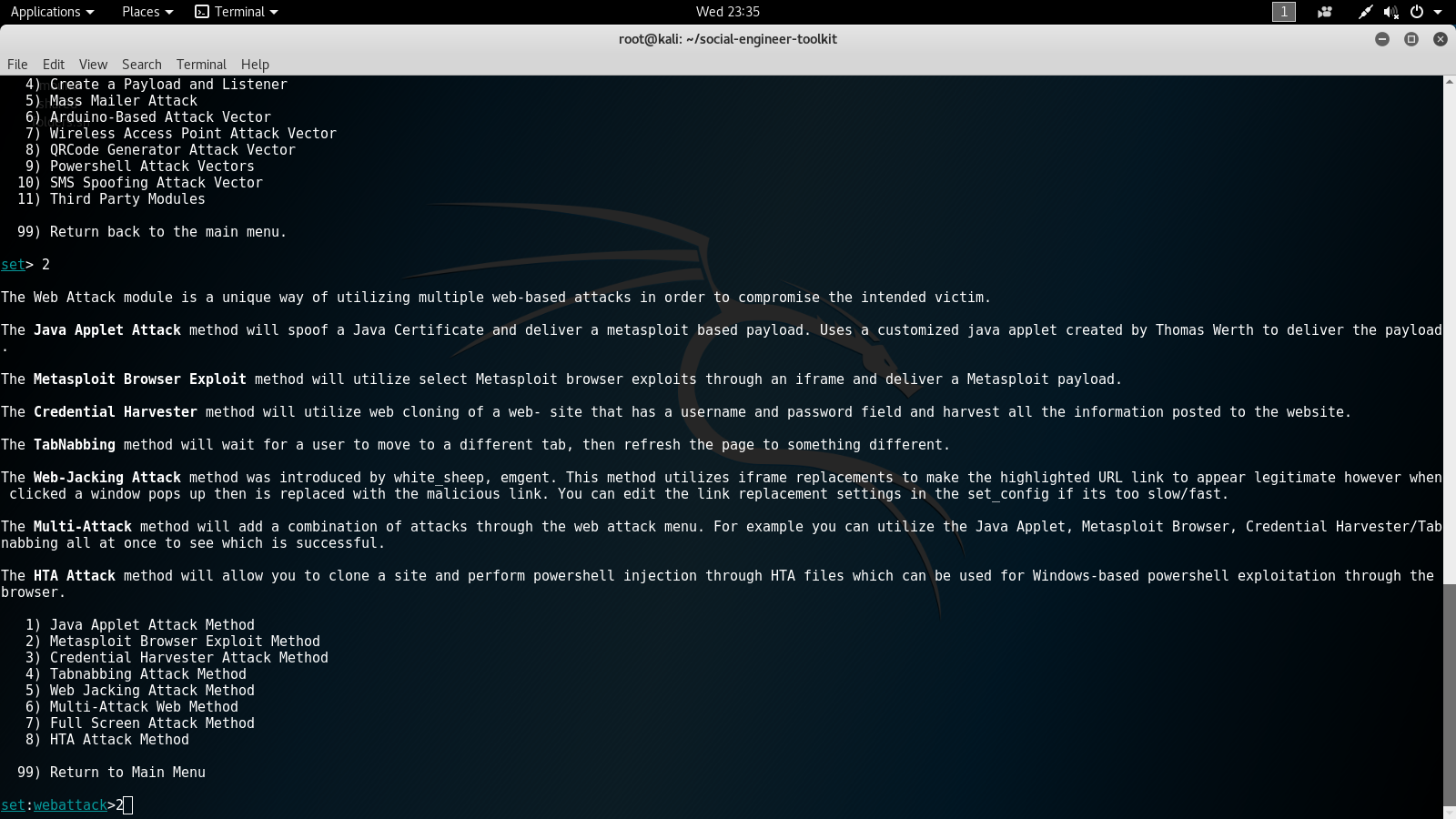
- In the next options menu, we will select number
1forWeb Templates...





































































